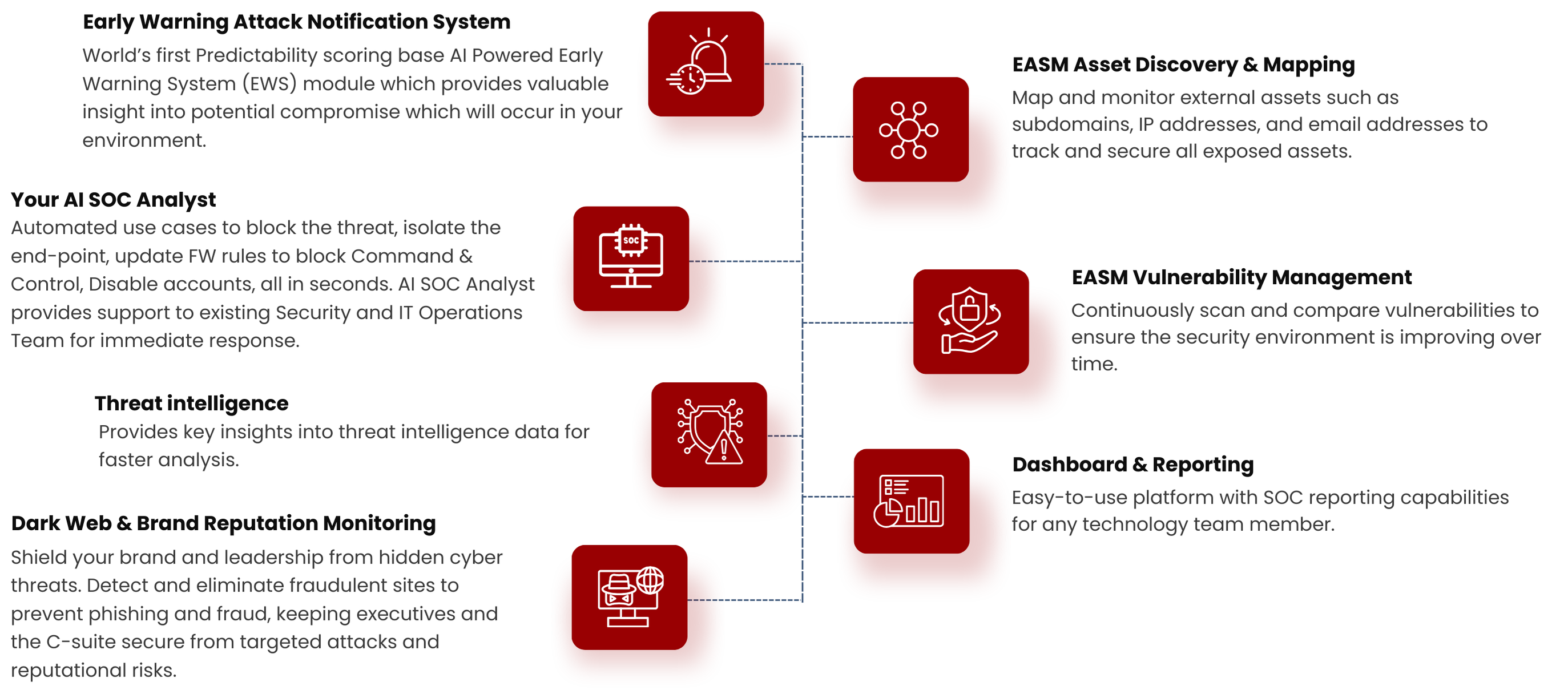
DarkSense Platform
about darksense
AI Powered Cyber Dome for Early Warning Threat Prediction, Prevention, Detection & Response
DarkSense is a cybersecurity platform powered by AI-generated predictability models to stay ahead of malicious adversaries. The platform is bolstered by Arancia’s best in class cyber team, providing 24x7x365 threat hunting and response services. Unlike traditional solutions, DarkSense is not reliant on human intervention to analyze alerts. Instead, it can be classified as a comprehensive cyber defense platform driven by AI-based data models, eliminating false positives and providing organizations with valuable data insights to take action and maintain a crucial advantage over the adversaries.
Utilizing a powerful blend of sophisticated AI driven predictability models, Dark Web monitoring and ingestion of key technology assets, DarkSense empowers your organization with the insights needed to stay ahead of adversaries targeting their next victim.

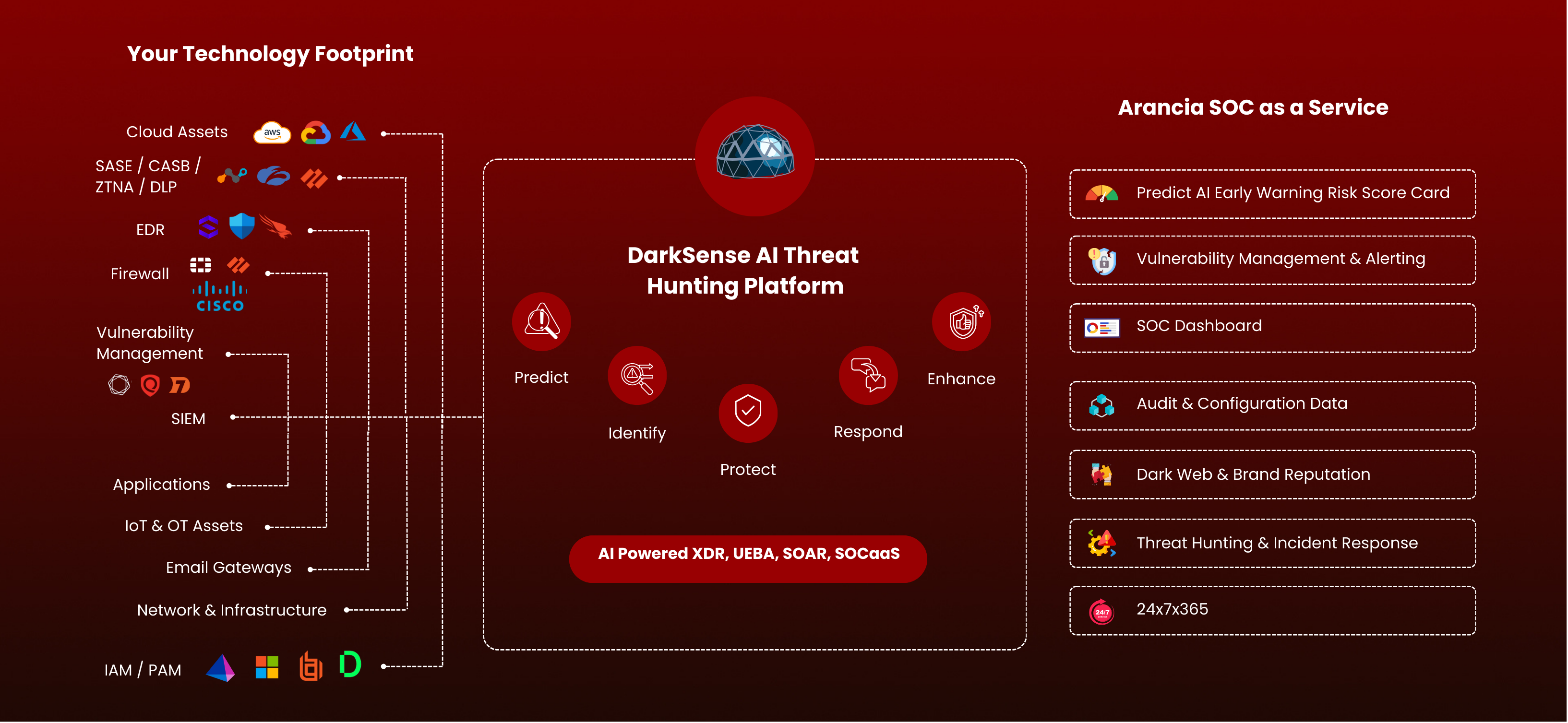
DarkSense Platform Differentiator
Arancia’s SOC as a Service (SOCaaS) with our AI Powered DarkSense Platform, enables organizations to leverage global Cybersecurity expertise, offering 24/7 managed security services. By implementing Advanced Early Warning System (EWS) models to predict when the next Cyber attack against your organization, DarkSense provides the unique ability to detect and contain within seconds, giving your organization the proactive defence structure to be resilient within an ever evolving threat landscape.

EWS (Early Warning System)
AI Powered advance Predictability Threat Intelligence & Data Models to stay ahead of Potential Threats

MTTD & MTTR (Mean Time To Detect and respond)
Minimizing the time taken to detect and respond to threats.

Ml & Anomaly Detection
Enhancing detection capabilities with advanced AI and ML technologies.

Security Orchestration, Automation, and Response (SOAR)
Streamlining and automating security operations to improve efficiency and response times.
Contact Us
Protect your digital assets with confidence. Contact us today for cutting-edge cybersecurity solutions tailored to safeguard your business against evolving threats.
- [email protected]
- 5255 Orbitor Dr #503 Mississauga, ON L4W 5M6